List of useful websites to check your security posture
October 23, 2023 —
Nico Cartron
Context
I recently stumbled upon Security Headers, thanks to a tweet by Stephen Rees-Carter.
I started looking at it, and found things I could improve (nice understatement, as you'll see below), but I figured out it would be nice to do a sum up of the security websites which can help improve your security posture.
securityheaders.com
- Scope: websites
- Goal: check HTTP security headers used on a specific website, and give recommandations
- Principle:
- the site "scans" your website and fetches the HTTP headers to see whether specific security ones are being used.
- it then gives you a grade, from A+ (very good) to F (not using any security headers)
- and then gives you recommendations: missing headers, and also upcoming headers, i.e. which will come soon.
I wrote a detailed article about it, explaining how I used it to secure my website.
dnsviz.net
- Scope: Authoritative DNS
- Goal: Check that DNS zones are properly configured, with a focus on DNSSEC
- Principle:
- dnsviz checks the whole DNS chain, and highlights the misconfigurations.
- Sum up: to me, dnsviz is THE DNS troubleshooting tool to use when dealing with DNS issues. It is now being maintained by DNS-OARC
dmarctester.com
- Scope: emails
- Goal: DMARC testing
- Principle:
- you send an email to dmarctester
- which looks at the various DMARC/SPF DNS records
- and tells you if it's well configured or not
- Sum up: very nice UI, and very didactic: the site shows and explains each step it takes:
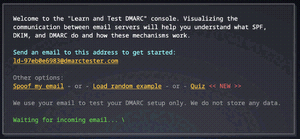
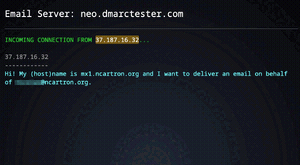
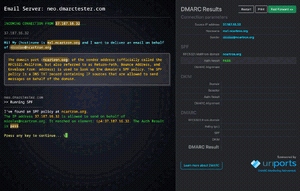

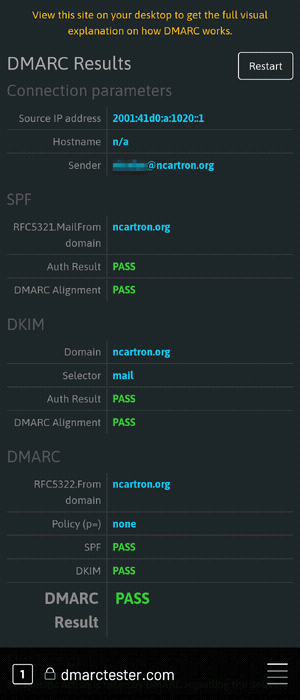
Note that it is also available over mobile, with a more minimalist UI:
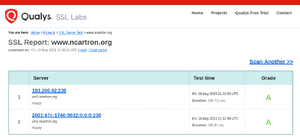
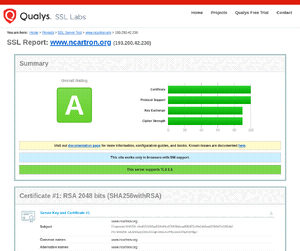
Qualys' SSL Server Test
- Scope: website
- Goal: analyse the configuration of a "SSL server on the public Internet"
- Principle: comparable to securityheaders.com - it scans your web server and gives it a grade, depending on how it is configured. It goes a bit deeper though, as it not only look at the security headers, but also looks at TLS certificate, supported protocols (TLS 1.3, ...), Cipher suites, ...
- Sum up: a good complement to securityheaders.com, as it gives more details on your TLS configuration.
Have I been p0wned?
- Scope: Passwords leaks
- Goal: Have I been p0wned lists all the security breaches that happened and led to passwords for various sites to be exposed.
- Principle:
- You enter your email address, and the site tells you whether it found it in a breach
- You can also subscribe to future updates: whenever a site gets compromised/passwords are stolen, you'll get an email notification to warn you, so that you can change your password.
- Sum up: also a site that you MUST subscribe to, to get alerted whenever one of the websites you're using has been compromised.
Wrap Up
I hope you found that list useful - I have probably forgotten many others, so please feel free to hit me on Twitter if you think one of them is worth adding to that article.