Securing your website thanks to securityheaders.com
It literally takes 5 minutes to do, let's see how to do it
Context
I recently stumbled upon Security Headers, thanks to a tweet by Stephen Rees-Carter.
I started looking at it, and found things I could improve (nice understatement, as you'll see below).
securityheaders.com
Created and maintainted by Scott Helme, its goal is to check HTTP security headers used on a specific website, and give recommandations:
- it does so by fetching your website's HTTP headers to see whether specific security ones are being used.
- it then gives you a grade, from A+ (very good) to F (not using any security headers)
- and then gives you recommendations: missing headers, and also upcoming headers, i.e. which will come soon.
Testing it
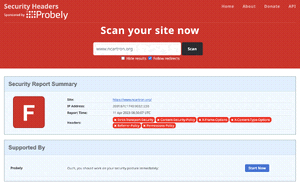
Let's start by testing www.ncartron.org - as you can see, the initial scan was not really great, since I got a F! And indeed, I hadn't implemented any of the security headers.
Improving my score
Strict-Transport-Security
I modified my Apache configuration to add Strict-Transport-Security, which allows enforcing the use of HTTPS: your web browser, once it has connected over HTTPS to a website, will refuse to "downgrade" to an HTTP connection next time it connects to this website, and will use HTTPS straight away.
You can enable it with the below in your virtual host configuration file:
Header always set Strict-Transport-Security "max-age=3153600; includeSubDomains"
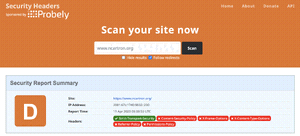
Testing again, and this time I'm getting a D, which, while far from perfect, is a bit better:
Content-Security-Policy
Let's now add Content-Security-Policy, with:
Header always set Content-Security-Policy "frame-src 'none'; script-src 'none'; default-src 'self'"
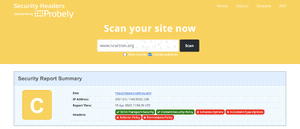
This is getting addictive, improving your score and getting different colors every time =)
X-Frame-Options and X-Content-Type-Options
I then added those 2 options, with:
Header always set X-Frame-Options "SAMEORIGIN"
Header always set X-Content-Type-Options "nosniff"
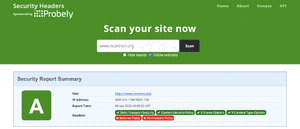
Now getting an A, much better, but the top score is A+, let's aim for it!
Referrer-Policy and Permissions-Policy
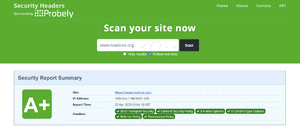
Finally, adding those 2 headers with the below configuration gave the A+!
Header always set Referrer-Policy strict-origin-when-cross-origin
Header always set Permissions-Policy "accelerometer=(), camera=(), geolocation=(), gyroscope=(), magnetometer=(), microphone=(), payment=(), usb=()
Broken content
I initially configured Content-Security-Policy with a script-src directive,
but found out that it was breaking Pagefind, the
excellent static search
engine running on
my blog.
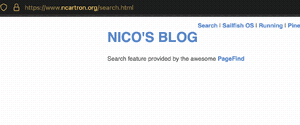
I have since removed that directive, until I find the correct settings.
Wrap Up
I'm really happy that I discovered securityheaders.com - it's been there for a while but I missed it, and it is really a nice and easy tool to strengthen your web server configuration - huge thanks to Scott for developping it!