SailfishOS as WireGuard endpoint
I finally managed to configure it, here's a quick guide
WireGuard Server
I used my OPNsense gateway as WireGuard server. I followed this excellent Road Warrior Setup from the OPNsense docs.
SailfishOS setup
Packages needed
You'll need the following packages from Openrepos:
- WireGuard for Sailfish (Settings UI)
- WireGuard for Sailfish (connman plugin), which will be installed by the above Settings UI package.
Configuration
Once you have WireGuard installed, head over to Settings > System > VPN, and use Pulley menu > Add new VPN:
- Select WireGuard:

- then "Skip" (unless you already have a configuration file you want to import)
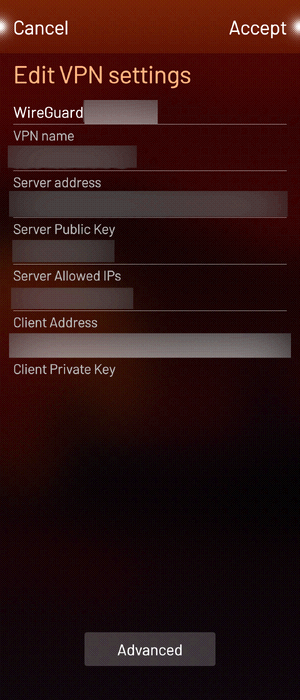
- you then have to enter the usual WireGuard endpoint parameters:
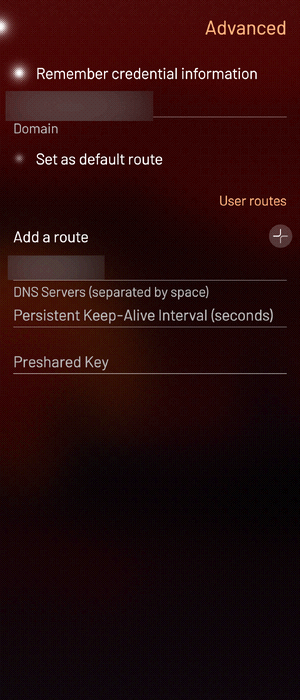
- in the Advanced section, you can specifiy the remote DNS server, as well as
add specific routes:
A note on Client Private Key
As the SFOS WG client cannot generate its own private key, you'll have to do it
yourself.
I did it on my FreeBSD laptop by installing the wireguard-tools-lite package,
and using this command:
wg genkey | tee private.key | wg pubkey > public.key
You'll need to use the contact of the private.key file in your SFOS configuration.
I lost 1 hour because I used the same public key as what I had configured on the OPNsense side, and didn't pay attention!
Testing the setup
You should now have a VPN entry, which is not connected - clicking on it will hopefully make it connect to your WG server:


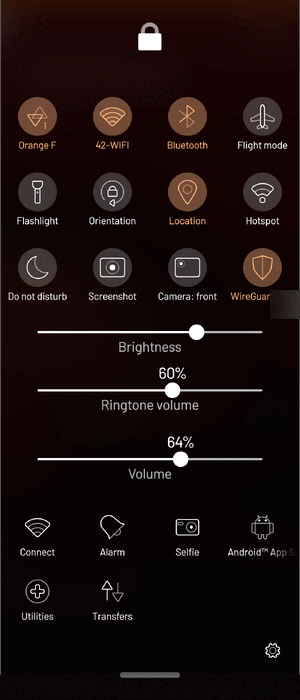
You can also add VPN to Sailfish OS' Top Menu, and connect/disconnect your VPN from there:
You should be able to connect to some of your resources, and you can also check
with netstat -nr or route print that the routing for those resources goes
through the VPN:
[defaultuser@Xperia10III ~]$ netstat -nr
Kernel IP routing table
Destination Gateway Genmask Flags MSS Window irtt Iface
0.0.0.0 192.168.1.1 0.0.0.0 UG 0 0 0 wlan0
85.18.26.73 192.168.1.1 255.255.255.255 UGH 0 0 0 wlan0
192.168.1.0 0.0.0.0 255.255.255.0 U 0 0 0 wlan0
192.168.1.1 0.0.0.0 255.255.255.255 UH 0 0 0 wlan0
10.42.22.0 0.0.0.0 255.255.255.0 U 0 0 0 vpn0
10.42.22.2 0.0.0.0 255.255.255.255 UH 0 0 0 vpn0
192.168.200.200 192.168.200.200 255.255.255.255 UGH 0 0 0 vpn0
Wrap Up
I wanted to set up WireGuard for a while, to replace my existing OpenVPN setup
which I found less and less convenient.
I'm glad I did it, and it took me significantly less time than what I thought -
even counting the 1 hour I lost with the wrong key :D
Tags: SailfishOS